What do Frank Abagnale Jr., the notorious con artist from “Catch Me If You Can”, the Golden Snitch from “Harry Potter,” and the Higgs boson from physics have in common? They’re all extremely difficult to catch. Whether it’s outsmarting the FBI, eluding a Quidditch player, or taking physicists almost 50 years to discover, each represents a challenge of capturing something elusive. This analogy perfectly illustrates the nature of sophisticated cyber threats targeting container environments today – they are designed to evade detection, making them incredibly hard to catch.
To help organizations address these challenges, Aqua provides Dynamic Threat Analysis (DTA), which has just received the official patent (No. 12001543) for its unique technology. This capability allows DevSecOps teams to timely detect malicious threats in their container images before they are deployed – effectively preventing them from causing any damage to production.
The Evolving Threat Landscape: Elusive as Ever
Today, the threat landscape for containers is increasingly complex, with attackers continually evolving and shifting their methods, adopting more advanced techniques to evade organizations’ security measures. Hot trends include the exploitation of public container images to conceal malware, the rise of software supply chain attacks, and the use of stealthy and polymorphic malware that activates only at runtime.
Traditional security tools, such as vulnerability scanners, have been essential for detecting known risks within container images. These tools are effective at identifying a wide range of risks such as known vulnerabilities, embedded secrets, excessive privileges, misconfigurations, and more. Aqua’s own open source scanner, Aqua Trivy, is a prime example of a robust tool that provides a solid foundation for reducing the attack surface of container images.
However, static scanning alone falls short against the more sophisticated and dynamic threats employed by today’s attackers. These scanners cannot detect malicious and suspicious behavior such as network anomalies, malware execution, container escapes, backdoors, fileless malware as well as novel, zero-day threats. For example, you might run an image from DockerHub that appears legitimate, but suddenly your CPU usage skyrockets. The reason is that the Docker image you downloaded was infected with malware.
Key takeaway: Vulnerability scanning alone is not sufficient to face the evolving threats targeting container environments today.
Going Beyond Vulnerability Scanning: Aqua DTA
Initially, Aqua DTA was developed inside the Aqua Nautilus research team to catch threats in container images that go beyond the capabilities of static analysis. DTA leverages a patented sandbox technology that combines signature-based detection with advanced behavioral analysis. This dual approach enables DTA to identify novel malware and zero-day attacks that static scanners miss.
Here’s how it works:
- Emulating containers: DTA pulls container images from registries like Docker Hub and runs them in a sandbox environment (a VM) to monitor how they would behave in production.
- Behavioral analysis: The beauty of DTA is that it doesn’t just look for known malware signatures. DTA watches for different signs of suspicious behavior, catching things like fileless malware and rootkits.
- Threat classification: Once it identifies malicious behaviors, DTA classifies them by risk score and maps it against the MITRE ATT&CK Framework, helping security teams investigate threats further and prioritize them for remediation.
The diagram below showcases how DTA conducts the analysis:
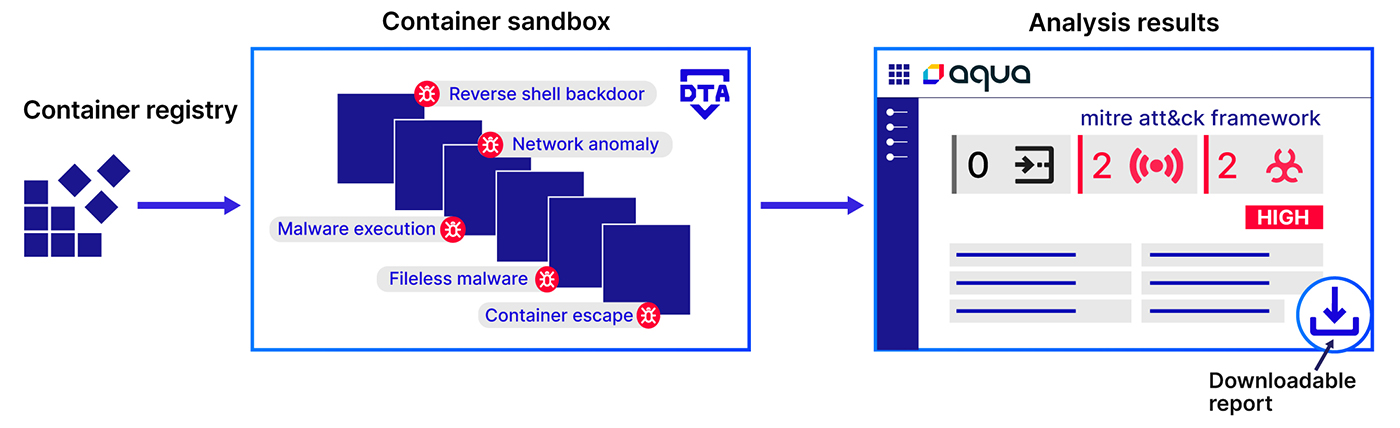
Figure 1: How DTA conducts the analysis
In a nutshell, Aqua DTA complements shift left vulnerability scanning by serving as an additional preventive control in the CI/CD pipeline, effectively catching known and unknown threats early in the application lifecycle before they reach production.
A Case Study: Detecting Evasive Attacks Early in the CI/CD Pipeline
Let’s explore how DTA works with a real-world example. The Aqua Nautilus Research Team reported an attack involving a fake Ubuntu Docker Hub repository, designed to trick users by adding a “z” to the end of the image name, mimicking legitimate Ubuntu images.
Unsuspecting developers would pull and run these compromised images in their environments. Once executed, an image would immediately download a cryptocurrency miner from GitHub, which would appear legitimate to traditional firewall solutions and bypass all static scanning controls.
Alarmingly, these malicious images have been downloaded and used over 330,000 times. DTA, however, would catch and alert about these threats before the images were deployed, preventing them from causing any damage to production.
Enhance Your Container Security with Aqua DTA
As the threat landscape continues to evolve, Aqua’s Dynamic Threat Analysis provides a critical layer of prevention for organizations looking to stay ahead of escalating threats. Its advanced behavioral analysis allows security teams to detect sophisticated threats that static scanners miss. DTA empowers teams to proactively stop threats before they reach deployment, preventing security breaches and minimizing the potential impact of attacks.
By integrating DTA into their larger container security strategy, organizations can effectively safeguard their applications against even the most elusive threats.
Join us on June 25th for our LinkedIn live webinar: Catch Me If You Can: Uncovering Malicious Behavior in Container Images