Let’s face it, the demands of modern application development put tremendous pressure on Dev. Just to keep up with production demands, most developers have to keep numerous images available in their registries. These images include production images, images being built and pushed regularly, recent “known good” images, outdated images, and more. With such a bloated store of resources, one of the major challenges that Dev faces is trying to scan only the images required for a particular deployment and avoid wasting time on irrelevant images.
To address this, we need to answer these questions:
Can I scan all the images pulled from my registry?
Is it possible to scan images in bulk during after-work hours to reduce the load on resources?
Can I scan just a subset of images (e.g., pre-prod only) from my registry?
How can I scan only recently created images?
How can I ensure already-scanned images do not have any new vulnerabilities?
Can I automatically rescan required images?
Can I avoid wasting resources and stop scanning images that are no longer used?
When looking at this list of questions, a common answer begins to emerge; you need an automated process for scanning only the images that you need within a given registry — at whatever frequency is required.
Rules-based image pulls offers a solution
Aqua provides the answer. Using rules-based image pulls offers a mechanism to automatically pull images from registries (based on some pattern) and then scan or rescan them at some scheduled time. There are several different elegant features offered by this solution that address a few areas of concern.
Let’s answer some of the questions we posed earlier:
Can I scan all the images pulled from my registry?
Yes, and you can do this automatically – The user does not need to manually add each image from registry for scanning. Instead, while integrating the registry – she can select “Automatic” pull and scan images. The rules selected under this section will determine the images that should be automatically pulled into the scan queue for scanning.
Is it possible to scan images in bulk during after-work hours to reduce the load on resources?
Yes, you can use schedule pull and scan jobs – The user can schedule an automatic pull and scan of images at the time she chooses. This ensures the job runs only when scheduled, without creating any added load on resources.
The Autopull schedule can be configured as shown in Figure 1.
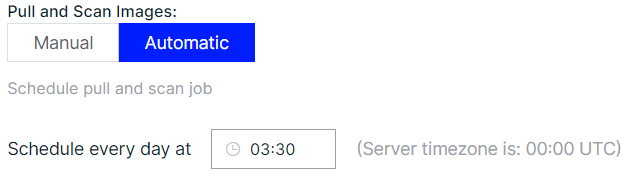
Figure 1: Schedule Autopull time
Can I scan just a subset of images (e.g., pre-prod only) from my registry?
Sure, with image pull patterns and exceptions – The user has the option to add different patterns to filter images to be pulled for scanning (even repeatedly). She might want to scan all latest images in all repositories, all pre-prod and prod images, all-new dev images that have been added on that day, and many other combinations. She also might want to always scan some critical images and never scan any unstable images. Thus, depending on a pattern in the repository or tag in the image – the user can specify the images to be scanned, without having to depend on explicitly naming each image. See figure 2.
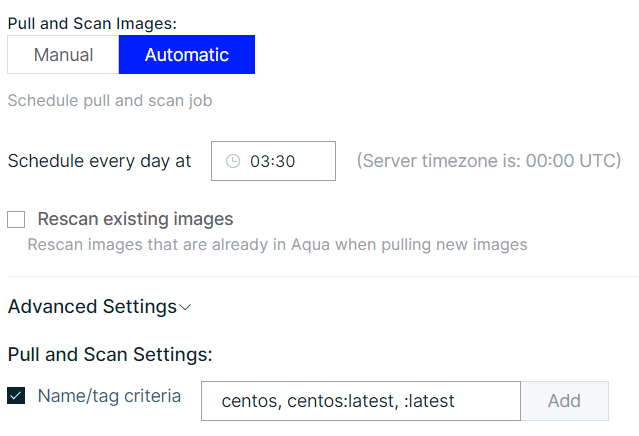
Figure 2 Pull Pattern
<name><:tag> If the text string name (e.g., pre-prod) is specified, only images with names containing name will be selected. If the text string tag (e.g., :latest) is specified, only images with tags containing tagwill be selected.
Examples:
pre-prod will select all images with a repository containing pre-prod substring
:latest will select all images whose tags contain latest
prod:stable will select all images with a repository containing prod AND tags containing stable
Exceptions to consider while pulling images, users can also use the same format of patterns under the exceptions sections to specify images that she always wants to pull or never wants to pull.
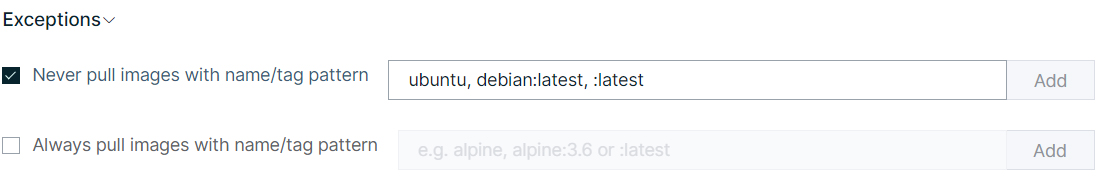
Figure 3 Exception Patterns for Autopull
How can I scan only recently created images?
The answer is with image creation time criteria – In situations where a user has registries with a huge number of images, chances are high that some will be outdated and no longer used. Most of these images can be classified by their creation dates – the older the creation date, the more likely the image should be deprecated. Here, the user can specify image creation time criteria, which filters images based on your selected date conditions (days/months/years). For example: if a user selects 60 Days, only images created in the past 60 days will be pulled, as shown in figure 4.
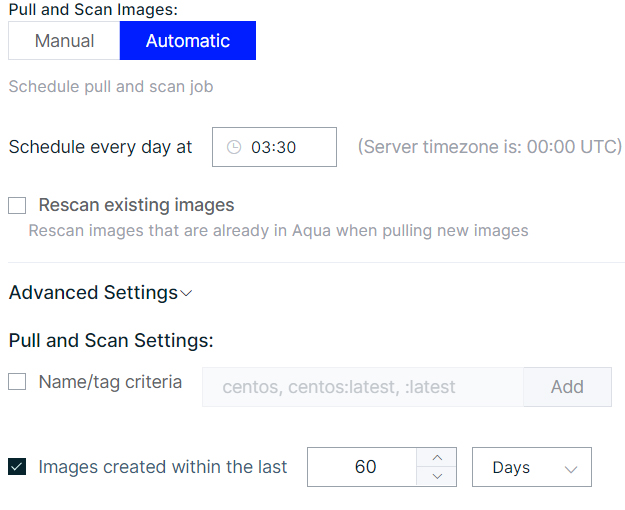
Figure 4 Image creation time
How can I ensure already-scanned images do not have any new vulnerabilities? Can I automatically rescan required images?
Yes, you can automatically rescan existing images for new vulnerabilities – Under certain circumstances, as is the case when a new vulnerability is reported against a resource within an already-scanned image, the rescan will identify and list the latest vulnerabilities requiring remediation. Once the parameters are selected, the job will automatically pull the images from registry if there is a change/update in the image in the registry.
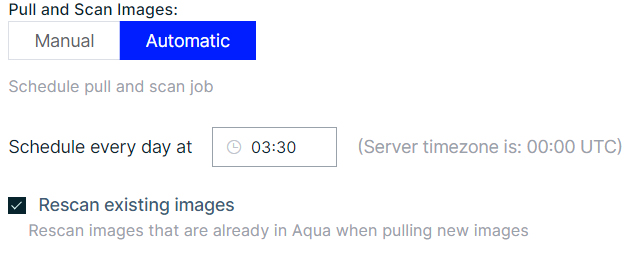
Figure 5 Rescan using Pull and Scan Images window
Can I finally avoid wasting resources and stop scanning images that are no longer used?
Yes, using rules-based image pulls from Aqua Security means no more wasting time!
Additional features in the Aqua’s vulnerability scanning:
Support for Multiple Registry Types:
- Docker Hub
- Azure
- Amazon EC2
- CoreOs Quay
- Google Container Registry
- Harbor
- JFrog
- OpenShift
Supported registry intergrations
Enable Webhook configuration – For supported registry types, the user can configuration automated pulling and scanning of images added or modified in the registry. If enabled, the registry will push notifications about any changes in an image (newly created, existing, or modified images) and immediately pull and scan the images.
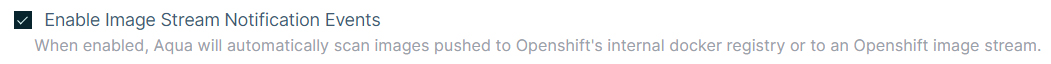
Figure 6 Enable Image Stream Notification
Concurrency/Performance – As many users need to scan large numbers of images every day, we have included concurrency as part of this process. Using concurrency, the Aqua solution can pull over 100K images from registry within minutes and push to the scan queue and scan.
Summary
If you’re tired of dealing with the bloat of images in your registries and want to stop wasting time and resources on unnecessary scans — then scanning registries at scale with rules-based image pulls provides the solution.

