The AWS Security Hub SecOps tool provides a comprehensive view of security and compliance alerts across various AWS accounts. Security findings are collected and summarized on integrated dashboards, allowing security professionals to continuously monitor their environment using automated compliance checks. The Aqua Cloud Native Security Platform collects security insights that are unique to the development, packaging, and runtime of cloud native applications, providing full visibility and control over cloud native workloads. The integration with AWS Security Hub provides granular visibility into vulnerabilities and threats in cloud native applications, whether their workloads are running on Amazon ECS or EKS, or any other orchestration platform.
Sending Aqua insights to AWS Security Hub closes the gap in visibility and allows security teams to respond to threats faster and make more informed decisions on how to manage risk.
Unique Security Insights from Development to Production
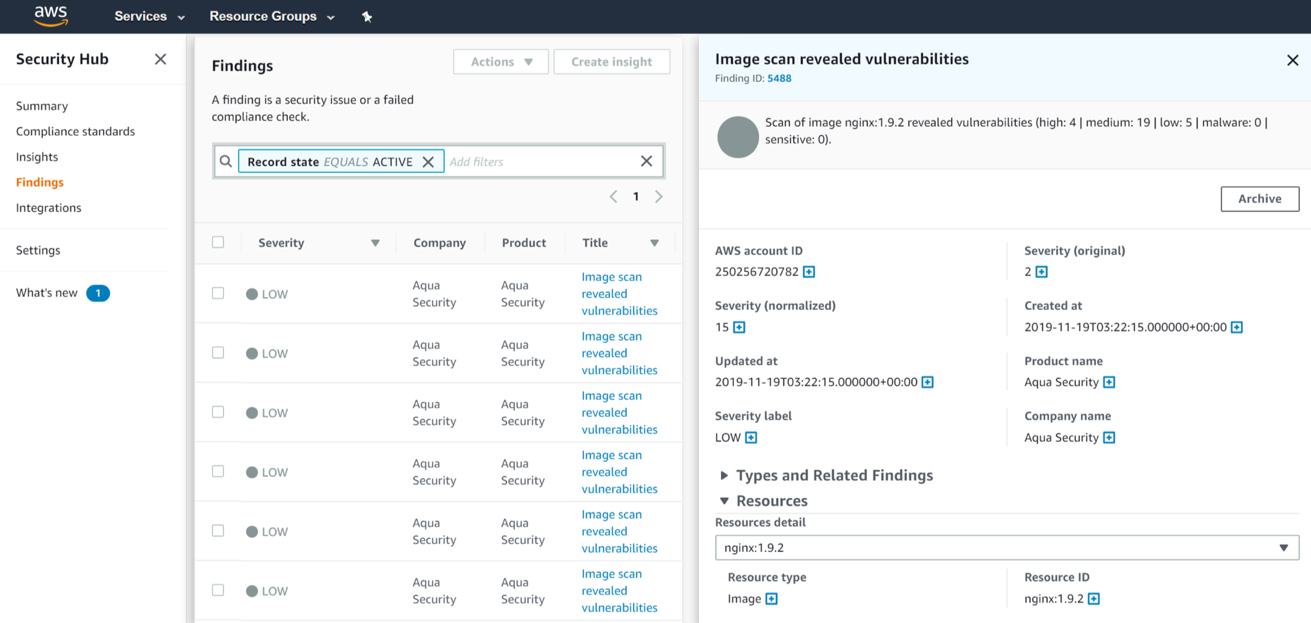
Aqua begins securing container applications long before container images are pushed to the runtime engine (e.g., Amazon ECS, Amazon EKS) by plugging into the user’s CI/CD tool of choice and scanning through the build process to identify and block risky images before they’re published to a container registry. Aqua will then continuously scan the registry to find risky images and flag them as noncompliant, notifying the relevant development team, and blocking these images from being pushed into production. Risky container images and their corresponding vulnerabilities are then reported through the AWS Security Hub dashboard.
The Aqua image assurance functionality also tracks attempts to push images to the runtime environment, ensuring that failed or unregistered images are prevented from being pushed into production. Any attempt to ship these images to the production environment will again issue alerts through the AWS Security Hub.
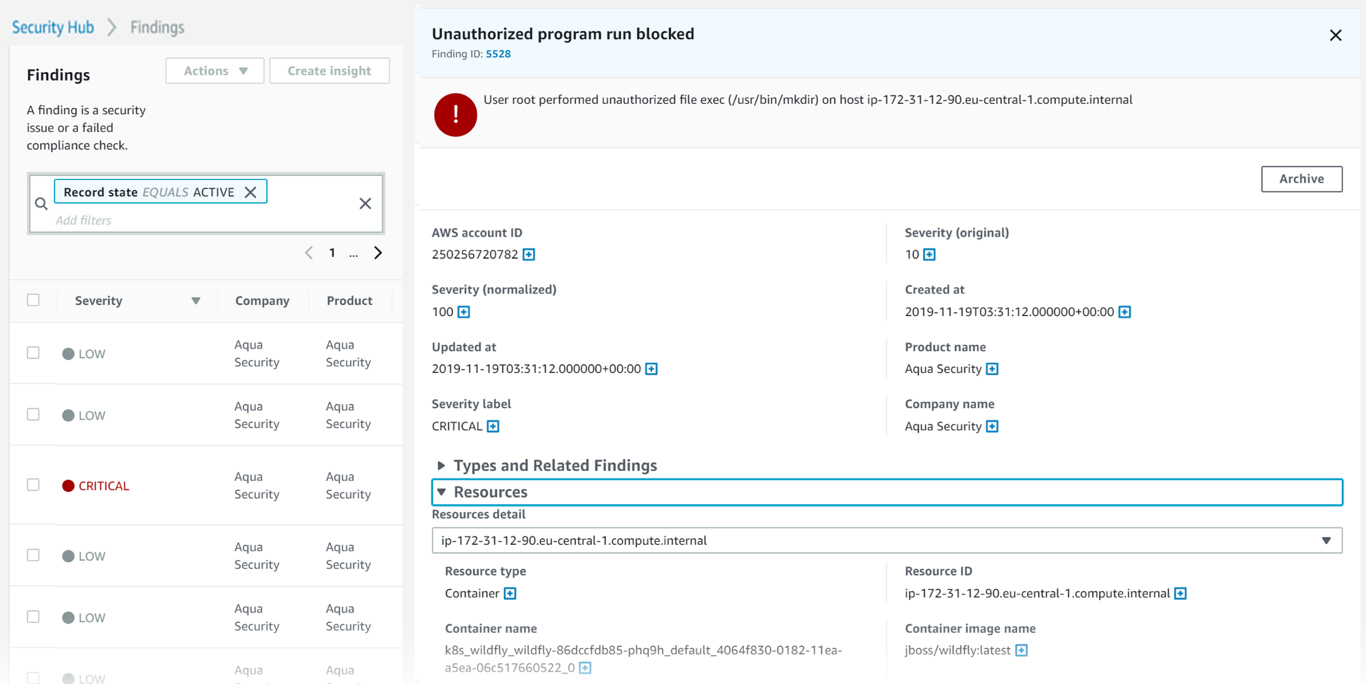
Unlike virtual machines, containers are meant to remain immutable in runtime, meaning they should not be changed once deployed to the cluster. Any changes made to the application, even simple re-configurations, ought to be made by the developer in the build phase and then pushed into production through the same CI/CD mechanism. To ensure container immutability, Aqua whitelists intended container activity in development and ensures that no executable deviates from that activity in runtime. If a suspicious or unauthorized attempt is made to change a container in production, that executable will be blocked without any container downtime, and an alert will be sent to AWS Security Hub.
Containers normally serve just one purpose, making their network behavior rather predictable. As such, Aqua also monitors that predictable network behavior to block unauthorized network connections and sends network activity alerts through AWS Security Hub.
Simple Setup & Configuration
The Aqua integration with the AWS Security Hub is free to use and does not require any changes to an existing Aqua license. In this case, the AWS Security Hub is implemented as a “sidecar” container. Users can leverage a CloudFormation template to install the integration and make any necessary configuration changes (e.g., IAM roles). Once the plug-in is installed, Aqua will immediately begin sending its findings to the AWS Security Hub.
Next Steps
The Aqua integration with AWS Security Hub, in addition to the multitude of AWS service integrations across the application lifecycle, enables developers to build, manage and monitor their applications quickly and securely.